Summary
Illegal robocalls are a nuisance and a vehicle for bad actors to commit fraud. The recent surge in robocalls is due to the accessibility of tools that enable fraudsters to spoof outbound dialing numbers and effortlessly generate millions of calls. This has led to consumers losing trust in phone calls.
STIR/SHAKEN is a series of protocols and a governance framework that ensure caller ID has not been spoofed, ultimately reducing the number of illegal robocalls. The industry began with STIR and has added SHAKEN to address this problem.
History of STIR
STIR, or Secure Telephony Identity Revisited is a set of technical standards developed by the Internet Engineering Task Force (IETF), which verify that a calling party is authorized to use a specific telephone number.
SIP was introduced in early 2000s, and as SIP adoption increased, so did robocalls. To address the growing issue, the IETF turned to cryptographic tools that provide a way to assert a caller’s identity by using certificates to authenticate the caller. However, STIR did not define the ecosystem or establish how carriers should implement these standards.
History of SHAKEN
SHAKEN, or Signature-based Handling of Asserted information using toKENs, is a framework developed by the Alliance of Telecommunications Industry Solutions (ATIS) for service providers to use when implementing STIR-using IP networks. SHAKEN introduces a governance model that designates the roles and responsibilities of the policy administrator (STI-PA) and certificate authority (STI-CA), and it outlines who is eligible to receive certificates (US carriers with OCNs).
It also defines additional data fields not included in STIR that enable traceback capabilities and a level of trust (attestation) based upon the carrier’s relationship to the telephone number.
How Does STIR/SHAKEN Work?
The Players
Federal Communication Commission (FCC):
Primary authority for Communications law, regulation and technological innovation. Composed of 5 members who are appointed by the President and serve a 5 year term.
Governance Authority (GA):
acts as a board of directors that influences policies and standards. The GA is made up of industry representatives from carriers (large and small) and equipment manufacturers.
Policy Authority (PA):
The PA is a trusted steward selected by the governance authority that
manages the enforcement of issuing tokens to carriers. To enable STIR/SHAKEN, a carrier needs to first obtain a token from the PA to prove it is an authorized service provider.
Certificate Authority (CA):
The certificate authority are trusted third parties approved by the PA that issues certificates to carriers wishing to originate calls. To ensure the requestor is eligible for a certificate, the CA first validates the credentials of the organization requesting the certificate with the PA.
Originating Service Provider:
As part of STIR/SHAKEN specification, the originating service provider is the service provider that attests to ownership of a phone number that originated from its network. This enables the terminating service provider to “trust” that the call was originated from a valid source and was not spoofed.
Terminating Service Provider:
This is the service provider that has a relationship with the call recipient. The terminating service provider validates that the call information has not been tampered with and completes the call.
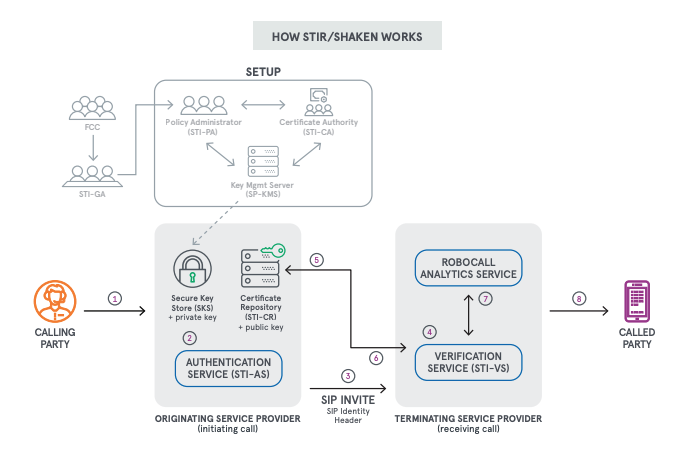
The Setup
The originating service provider obtains a token (credentials) proving it is who it says it
is, and then shares with the CA to get a certificate. The token is a form of identity that
enables the carrier to receive a certificate that allows the originating service provider
to digitally sign its calls.
Below are the steps required:
- Originating service provider requests a token from the PA
- PA grants originating service provider a token
- Originating service provider sends the token to the CA and requests a certificate
- CA validates the identity of the originating service provider requesting the certificate with the PA
- Originating service provider generates a key pair
- CA wraps a certificate around public key and sends to the Originating Service Provider
- Originating service provider uses the certificate to authenticate (sign) calls
This process establishes a chain of trust so that the recipient of the call can be confident
that the caller ID has not been tampered with.
Now What?
STIR/SHAKEN utilizes a combination of technical, legal, and behavioral solutions; it’s an evolving process that continues to be refined in order to address the dynamic needs of the marketplace.
Expected upcoming improvements include the support of non-IP networks, enterprise multi-carrier implementation, and standardizing how attestation is displayed on devices.
What do you need to Do?
In short, Nothing!
In anticipation of these industry-wide changes, our network has already been made compatible with the new standards. We have completed audits with all of our Interconnected Call Termination Partners to ensure that they are able to accept TOKENS and process them.
As long as all of your numbers are originating from our network, you will experience little to no change to your day-to-day experience.
